Two-Factor Authentication: “What?” and “How?”
With all the press about the Heartbleed OpenSSL vulnerability in the news, you probably don’t need another recount of why this is a big deal. If you’ve been following closely, you’re probably a bit freaked-out, and at the very least, have checked with all your online account providers to verify they were not vulnerable, have already addressed the issue, or are actively working on it. You’ll want to follow their instructions, and change your passwords if they were vulnerable, are fully patched, and have changed out their certificates. If you haven’t yet caught-up on all this, I’ll wait…then I’ll brief you on the added layer of security, called Two-Factor Authentication, you can add to your Google, Facebook, Linkedin, and Twitter accounts to help insure that, even if your passwords are forcefully acquired by some d-bag baddie, your accounts remain safe.
Passwords, even highly complex ones over an encrypted channel (like SSL/TLS), are not enough by themselves to secure important data. One of the cool tricks I used to show the students in my graduate classes was how easy it was to capture passwords using brute force methods using just a single, high-powered laptop. Even without brute force tools and access to the encrypted passwords, people have a bad habit of using simple words, family or pet names, important dates, or combinations of them to create passwords…stuff that is easily guessable if you have a little time on your hands. If someone manages to get your password, say, through diligent social engineering and research, or via a software vulnerability like Heartbleed, game-over…if you don’t have another layer of protection.
Before I go any further, I should say that what I am about to share on Two-Factor Authentication IS NOT a substitute for password sanity. Passwords should always be reasonably complex (at least 8 characters, mixture of alpha case, numbers, and symbols), you should never use the same password for all your accounts, and you should change your passwords periodically…even if you have additional layers of protection. If you aren’t a password savant, there are lots of cool tools out there, like LastPass, that not only help you store and recall your passwords, but can help you generate secure ones when you need to as well.
Two-Factor Authentication: “What?”
Sometimes when I start talking, I get looks from my friends that clearly express, “What the eff are you talking about now?” Two-factor authentication is a cool technology with some geek cred, but it’s also one of those things that sounds much more complex than it actually is. It basically just changes your authentication to being reliant on two things instead of just one. You still have the something you know, your username and password, but to that gets added something you have, which is a time-based, one-use, random token to verify your identity. So, each time you log in to your account, you have to enter in the normal stuff you know, but are also prompted for a time-sensitive, multi-digit code that a security device generates for you. Simple, right? Except now you’re thinking, “Security device? What do I have to buy now?” Fret not, my friend…you already own it. Most sites you use everyday can now provide authentication tokens for Two-Factor Authentication via SMS text message or app using your mobile phone.
Two-Factor Authentication: “How?”
Before we dive into how, probably should clarify some nomenclature. Two-Factor Authentication can also be referred to as Multi-Factor Authentication or Two-Step Authentication. Further, Google, Facebook, Linkedin, and Twitter all call Two-Factor Authentication something a little different. Google calls it “2-Step Verification”. Facebook refers to it as “Login Approvals” via “Security Codes”. Linkedin calls it “Two-Step Verificaiton for Sign-in”. Twitter uses “Login Verification”. It’s all the same stuff, so not to worry.
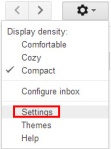
For Google, you will need to go into your account Settings. From within your GMail account, click on the cool little gear thingy, and select “Settings”.
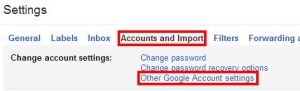
This will take you to the Settings page, where you will want to select the “Accounts and Import” tab, then click the link to “Other Google Account Settings”.
This will take you to a second Settings page. Select the “Security” tab, and you will be able to enable “2-Step Verification”. You can either use your SMS text messages to your mobile device for obtaining the tokens, or you can use the mobile app, Google Authenticator.
The “Settings” for 2-Step Verification take you to the page where you control how you get your verification codes (via Authenticator or SMS text message to your phone), specify application-specific passwords for cases where the 2-Step Verification codes will not work, an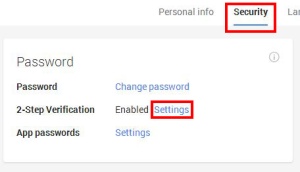 d obtain the printable, one-time use codes for backup purposes (don’t skip this step…when I changed phones, because I opted to use Authenticator, I needed these to unlock my accounts and
d obtain the printable, one-time use codes for backup purposes (don’t skip this step…when I changed phones, because I opted to use Authenticator, I needed these to unlock my accounts and 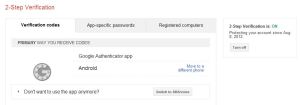 transfer control to my new device). You will, of course, want to keep your printed backup codes in a safe, but reasonably accessible place.
transfer control to my new device). You will, of course, want to keep your printed backup codes in a safe, but reasonably accessible place.
For Facebook, you will need to go into your account Settings through the drop-down menu on the right-hand side of the screen. Just click “Settings”, and on the resulting page, select the “Security” tab, and check the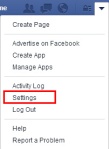 box to “Require a security code…”. If you’ve not associated a mobile phone number with your Facebook account yet, you will need to do that (you can keep the number private if you wish). You can also use the Code Generator in the Facebook Mobile App to get codes instead of relying
box to “Require a security code…”. If you’ve not associated a mobile phone number with your Facebook account yet, you will need to do that (you can keep the number private if you wish). You can also use the Code Generator in the Facebook Mobile App to get codes instead of relying 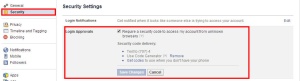 on SMS text messages. Like Google, you have the ability to collect backup codes to use in the event you do not have access to your phone.
on SMS text messages. Like Google, you have the ability to collect backup codes to use in the event you do not have access to your phone.
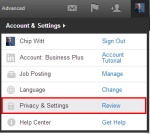 Linked in is a bit trickier to find, but is also pretty straight-forward to configure. Find the drop-down menu under your little picture icon in the upper-right-hand
Linked in is a bit trickier to find, but is also pretty straight-forward to configure. Find the drop-down menu under your little picture icon in the upper-right-hand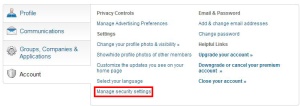 corner of the screen. Select “Review” next to Privacy & Settings. On the resulting
corner of the screen. Select “Review” next to Privacy & Settings. On the resulting
page, select the “Account” tab, and click on “Manage security settings”. The resulting page allows you to enable Two-step verification for sign-in. 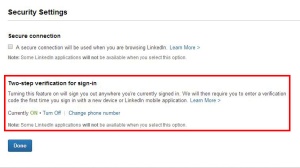 Again, you will be required to associate your mobile phone with your account.
Again, you will be required to associate your mobile phone with your account.
 You are probably sensing a theme. For Twitter, go to “Settings”, find the “Security and privacy” tab, then select the radio button for “Send login verification requests to…”. Once
You are probably sensing a theme. For Twitter, go to “Settings”, find the “Security and privacy” tab, then select the radio button for “Send login verification requests to…”. Once again, you will need to associate your mobile number with your account for all this to work. If you’d prefer not to use SMS text messages, you can enable “Login verification” in the “Security” section of the mobile app settings, and the app will provide the tokens for verification. You will be able to generate backup codes from the web settings page, and again, that is advisable if you are using the app instead of text messages, or expect you may be separated from your phone when you need access to your account.
again, you will need to associate your mobile number with your account for all this to work. If you’d prefer not to use SMS text messages, you can enable “Login verification” in the “Security” section of the mobile app settings, and the app will provide the tokens for verification. You will be able to generate backup codes from the web settings page, and again, that is advisable if you are using the app instead of text messages, or expect you may be separated from your phone when you need access to your account.
Two-Factor Authentication is a nice technology for adding an additional layer of defense that, while probably not invulnerable to specific types of attack (say, someone gains access to your mobile phone), gives you a bit of confidence that someone will really need to work hard to compromise your account. There are additional features you may want to enable in addition to 2FA. Facebook provides “Login Notifications” that can alert you via email or text message anytime your account is accessed from a web browser on a computer or device you’ve never used before. Twitter has a nice feature that forces your account to “Require personal information to reset your password”. Personal information in this context is your email address or mobile phone number.
Those that think you can be too secure haven’t been paying attention. Cyber-crime is on the up-swing, and the perpetrators are getting smarter, faster, and hitting their victims where they live. The OpenSSL vulnerability was an accident in coding. It’s not the first, and certainly won’t be the last. No software is perfect, and the bad guys are gonna do all they can to exploit every opportunity. It is up to all of us to do all we can, use all the tools at our disposal, and protect ourselves as best we can.
Stay safe!
Categories