
I was recently asked by someone what interesting things I had done with a Raspberry Pi. I remember a day when I could have rambled off a full list of experience, cautions … Continue Reading Catching the Raspberry Pi Fever

Very occasionally a tool or software package stands-out to me on the pure virtue of being the right solution at the right time. If it happens to do exactly what … Continue Reading Unbound…A Truer Word Has Never Described Software

A while back I did extensive research (even for me) on desktop speakers, and found amazing quality at a price that was still affordable in the Studiophile AV40 kit from … Continue Reading Rockin’ Out Wirelessly with Bluetooth

With all the press about the Heartbleed OpenSSL vulnerability in the news, you probably don’t need another recount of why this is a big deal. If you’ve been following closely, … Continue Reading Two-Factor Authentication: “What?” and “How?”

Most Android devices, Smart Phones and tablets alike, come with some built-in capabilities for automating different types of tasks. Useful lifestyle enhancers, like being able to set periods of time … Continue Reading Tasker for Android
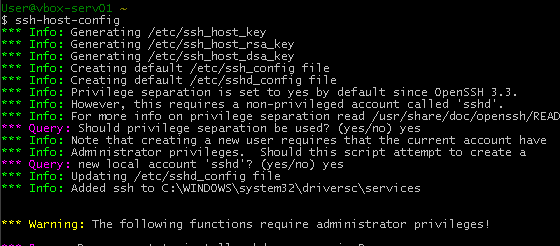
As someone that was openly critical of Windows Vista during its short reign as the flagship Microsoft product, mostly due to my experiences bailing out friends and clients that had gone down … Continue Reading Configuring Windows 7 for Remote Access with Cygwin sshd

Man, how times change. I remember paying nearly $200 for a 2GB USB flash drive in 2006, and having people “oooh” and “ahh” about the amount of storage space available … Continue Reading Booting via USB Key Made Easy
There are several tools and processes I’ve been wanting to make the subject of Weblog posts, but keep I forgetting about them until something comes up that makes me wish … Continue Reading favicon.ico Creation and Screen Captures on Linux
BCP, or Business Continuity Planning for long, is the art practiced to insure that when disaster strikes, your business doesn’t crumble. It can, and should include such things as site evacuation plans, … Continue Reading BCP and the Small Business: Computing Infrastructure
I have to admit, I love thinking that others read my weblog posts, and actually find them semi-useful…but realistically, I write them to leave my increasingly feeble mind breadcrumbs for … Continue Reading Mount an SMB/CIFS Share via Linux Automount







